185.63.2253.200: Everything About This IP Address
In this digital Era IP Address is one of the main components in the internet communication and data exchange between individuals and businesses across the globe. Every internet connection has a unique IP address which can be considered as a unique identifier. All the devices connected to some internet connection will have the same IP […]
Essential Security Measures for Protecting Your WordPress Site
Securing your WordPress site is an essential task to safeguard your content, protect user data, and maintain the trust of your visitors. A comprehensive security approach includes using CAPTCHAs, implementing login lockdowns, scheduling backups, managing resets, setting up maintenance mode pages, and leveraging .htaccess files. Captcha Security CAPTCHAs are effective tools in preventing automated bots […]
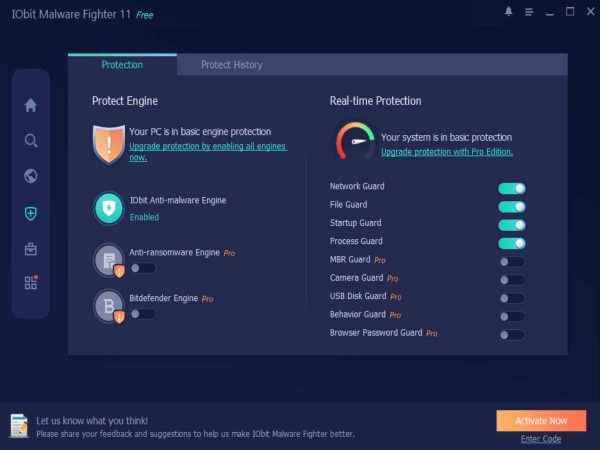
IObit Malware Fighter 11 Free: An Exceptional Solution for PC Protection
Strong anti-malware program IObit Malware Fighter 11 Free guards personal computers against a broad range of hazards like viruses, ransomware, spyware, and more. It is a great choice for consumers wishing to improve their system security without paying expenses because of its simple interface and extensive capabilities. Examining IObit Malware Fighter 11 Free’s features, advantages, […]
SIEM Evolution: Anticipated Transformations in 2024
Security Information and Event Management is a key tool in threat detection and response. With 2024 on the horizon, we will explore the key trends and factors that will change the SIEM landscape.This article will examine these key trends and emerging changes in detail and provide an overview of what to expect in the SIEM […]
What Actually Happens When Your IT System Is Hacked?
Cyber-attacks are a real and persistent threat to businesses. Every week, there are news headlines about yet another data breach or hack. Unfortunately, this is unlikely to change anytime soon. Hackers are getting more sophisticated, and IT security systems must work much harder to keep up. Although hacking is something most of us have heard […]
Phishing With AI – When Human Weakness Is Exploited With Technical Advances.
Digitalization has changed our daily lives and also the way companies conduct business. However, with the benefits of technology also come new risks. Phishing is one of the biggest cybersecurity threats and can have significant consequences for companies. A worrying development has emerged in recent years: phishing attacks are increasingly being combined with artificial intelligence […]
Explore The Advantages of Migrating To The Cloud, Cost Savings, And Scalability For Businesses.
Benefits of Cloud Migration with Managed IT Service An electrifying transformation is taking place in Houston, a place where innovation meets tradition. It is not about sprawling skyscrapers or bustling markets but about dominating the digital realm. Businesses of all sizes, including multinational corporations, are witnessing a new era illuminated by the vast potential of […]
10 Mistakes You May Be Making When Sharing Files
File sharing can be dangerous. But ask us to go back to the gloomy days of distributing USB sticks and DVDs and emailing large documents to coworkers? No chance! File sharing, collaboration platforms, and cloud storage services provide encryption and protection from hackers, with protected access and continuous syncing to make work easier. But if […]
Identity Theft On The Internet – The Keys To Respond
Phishing is a type of cyberattack that can get you into serious trouble. Sometimes, people with malicious intent track personal information that they later use to impersonate their victims in front of companies, institutions, or even others around them. On the plus side, this type of cyber threat, like most network risks, can be avoided […]
How To Protect Your Computer From A Computer Virus Attack
Regarding cybersecurity, some of the most frequent questions computer users ask are: will some type of computer virus infect my PC? How can I know that? What do I have to do if it is? It is a logical concern since nobody wants to see themselves in this situation. However, you have a series of […]